Customizing claims in ID tokens
Updated: July 16, 2020
This article contains instructions for populating your identity provider's ID tokens with custom user attributes. When you add a claim to your tokens, that claim can be used to populate attributes in your verifiable credentials.
Azure Active Directory
By default, Azure Active Directory ID tokens contain a small number of claims that can be used as attributes in verifiable credentials, such as preferred_username. These claims can be used in verifiable credentials without any additional configuration.
| Version | Link to Docs |
|---|---|
| Azure AD v1.0 tokens | ID tokens in Azure AD |
| Azure AD v2.0 tokens | ID tokens in Azure AD |
In addition to the default set of claims, Azure Active Directory also includes a set of optional claims that can be configured using the Azure Portal. Examples include tenant_ctry, upn, family_name, and given_name.
| Version | Link to Docs |
|---|---|
| Azure AD v1.0 tokens | Optional claims for v1.0 tokens |
| Azure AD v2.0 tokens | Optional claims for v2.0 tokens |
When you want to add additional user information to your tokens not available in the optional claims set, you need to customize the claims in your ID tokens. Configuring your Azure AD tenant to issue custom claims in its tokens is a three step process:
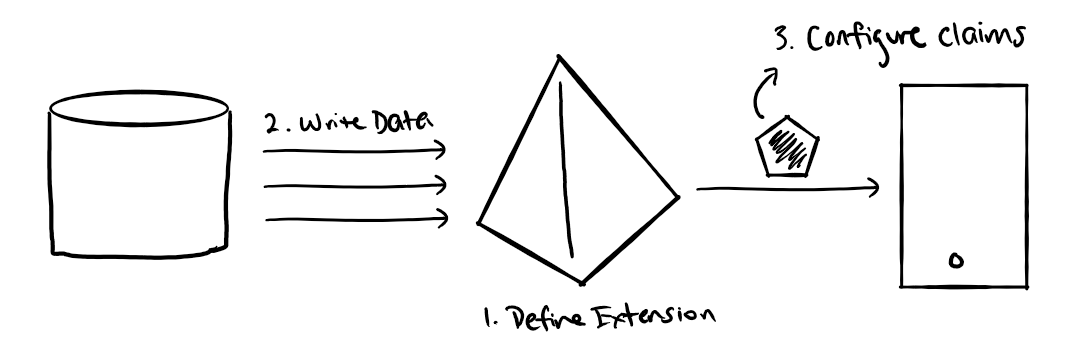
Once you have configured your ID tokens to include all claims necessary for your verifiable credentials, you can return to configuring your verifiable credentials.
Azure AD B2C
Azure AD B2C also includes built-in flexibility for customizing claims in ID tokens. For the purposes of issuing verifiable credentials, there are two approaches to consider.
Approach 1: Custom attributes in Azure AD B2C
Similar to the section above, you can extend your Azure AD B2C tenant with additional user attributes, and then populate your Azure AD B2C tenant with user data you wish to use in your verifiable credentials.
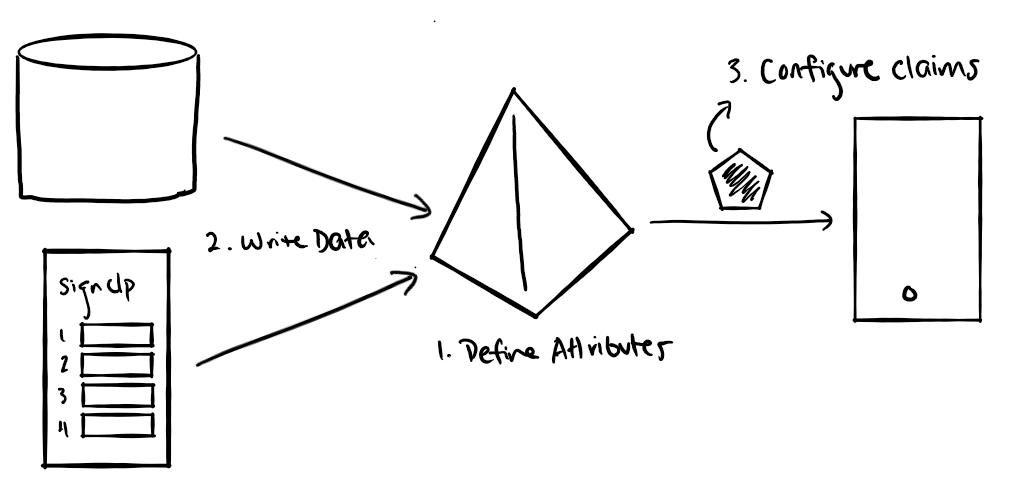
country, display name, email address, and many more. Configuring your claims to use these built-in attributes is quite simple. This article describes how to create a user flow in B2C and customize the attributes included in claims. If you want to include additional attriubtes, you can also easily define custom attributes for your B2C tenant and use them in your ID tokens.
Once you've poplulated those attributes with user information, they can be included in claims in ID tokens issued by your Azure AD B2C tenant.
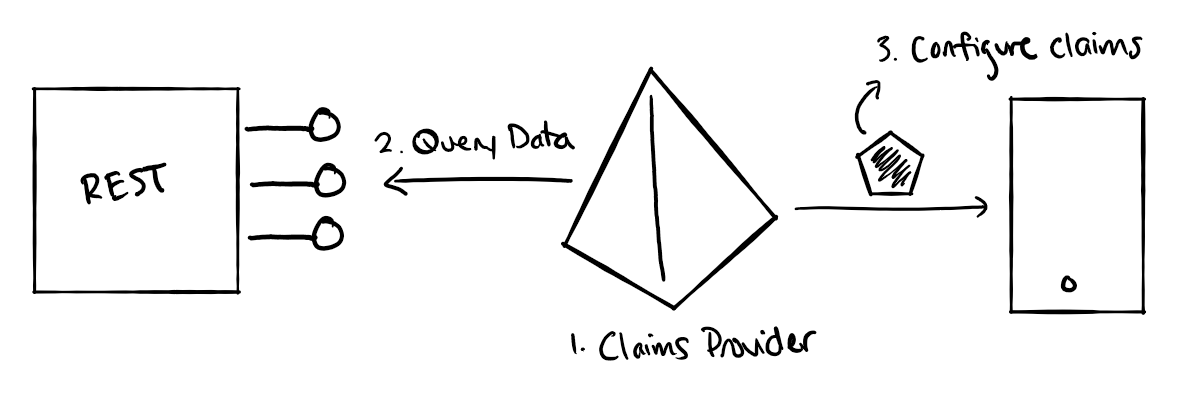
Approach 2: REST API exchanges in Azure AD B2C
Azure AD B2C also allows you to connect to an external REST API when issuing an ID token. The results returned from the REST API can be configured to be included as claims in ID tokens issued by your Azure AD B2C tenant.
Other identity providers
If you're not using Azure AD or Azure AD B2C to issue verifiable credentials, you'll need to figure out how to customize tokens issued by your identity provider. Contact us and we'll be happy to assist you in the process of integrating your identity provider with Microsoft Authenticator and Verifiable Credentials.
See something missing? We'd love your feedback and input on the Verifiable Credentials preview. Please contact us. When you use Microsoft DID Services, you agree to the DID Preview Agreement and the Microsoft Privacy Statement.